Stop Ransomware in Milliseconds.
Our unique anti-ransomware software deploys decoy files that detect encryption, alert you, stop it, then tell you where the process started.
$5/month for Dedicated Ransomware Protection
Learn More
Deploy Honeypot Files That Trap Ransomware
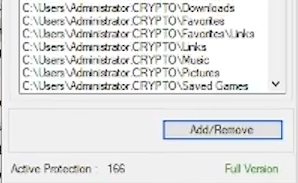
Choose Which Folders to Protect
Recover Up-to-date Data
Stop Ransomware in Milliseconds
Alerted To Where Attack Started
Recover Up-to-date Data
How Ransomware Kills Your Business
Rampant Attacks
Over 236 million ransomware attacks globally in the first half of 2022.
Windows is a Major Target
93% of all ransomware attacks were in the form of Windows executables.
USA is a Target
47% of global ransomware attacks targeted USA-firms. Most targeted globally.
Costs Millions
The average successful ransomware cost $1.85 million to recover from in 2023.
Ransom Cost Increasing
In 2021, the average ransom payed increased 144% to $6 million.
SMBs in Crosshairs
Mid-sized organizations paid an average ransom of $170,404 in 2021.
Extensive Downtime
The average downtime following a ransomware attack is 7 – 21 days.
Out of Business
60% of businesses that fall victim to ransomware close within 6 months.
How Our Business-Saving Ransomware Protection Works

Quickly Deploy
Zebra Ransomware Stopper (ZRS) takes just minutes to install. Simply download our .exe file, and select the folders you wish to protect.
We recommend protecting folders that have critical data that you cannot afford to lose.
If you require assistance, a member of team ZebraHost would be happy to help you install.
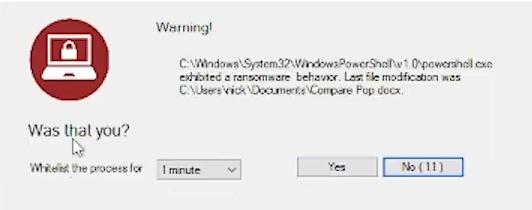
User Alerted
The moment a ransomware attack is detected via encryption or deletion, you will be alerted that an attempt was made, and thwarted.
Your notification will appear directly on the infected desktop as well as via email.

Ransomware Thwarted
ZRS thwarts any encryption or file deletion process immediately.
Once you choose which folders to protect, decoy files and deployed as invisible files within protected folders. If a process attempts to delete or encrypt them, the process is stopped. They form a barrier between ransomware and your important data.
Ransomware Report
After a ransomware attack is successfully stopped, we recommend you check the notification send to your email displaying where the ransomware process originated. This should lead you to where the ransomware is installed, so you can remove it.
We recommend you remove the ransomware, then gather unaffected files, so they can be moved to a new machine. This way, you can ensure the there is no dormant ransomware waiting to strike again.

