Most Notorious Ransomware in 2022 and History You Should Know

Since the first ransomware attack back in 1983, ransomware has continued to advance. In response to organizations enhancing security, and operating system developers increasing barriers between ransomware and your valuable data, ransomware gangs have made their software more dangerous and difficult to stop. Improvements include the method in which ransomware is injected, what permissions it has once on a system, which parts of the system become encrypted, and even how personal they make the attack.
There are countless ransomwares. Ransomwares are typically only active between several months to around 2 years before they are no longer actively maintained. But Ransomware as a Service (RaaS), a modern phenomenon where ransomware is sold on the dark web and the developer and attacker split the profit, has led to forking and dramatically increased the number of ransomwares available. So much so that there are now genres of ransomware!
While there are thousands of ransomwares that your business is exposed to, knowing a few of the most notorious ransomwares gives you an idea of how different ransomwares work. This list is by no means the only ransomwares you should be aware of but is a collection of well known ransomwares that are dangerous in 2022, or have historical significance.
Ransomwares You Should Know (Dangerous in 2022)
Petya
(Image Credit: Malwarebytes)
Petya is to date, one of the most dangerous ransomwares that can infect your system. The reason is that unlike more traditional ransomwares that infect individual files on your system, Petya goes after the master boot record for your PC and encrypts your hard drive file system. When you try to reboot Petya will hijack your boot and instead display a message that you must pay a ransom to reboot your PC. Petya renders the infected machine completely unusable.
A popular fork of Petya known as Notpetya makes the virus even more efficient. All that Notpetya needs a user to do is download the file and from there no manual interaction is required to encrypt the hard drive and force a reboot on the machine. Notpetya is considered a wiper rather than ransomware because it is not repairable. Instead, once a machine is encrypted by Notpetya, the only recourse is to restore from a backup.
Petya/Notpetya are still a threat and are easily forked. You should remain vigilent. Petya and Notpetya primarly spread via phishing emails.
Cerber
(Image Credit: Varonis)
Cerber is a network ransomware. It’s objective is to infect both the end-point it is installed on as well as any device connected on the same network.
What makes Cerber dangerous is that it does not target and can encrypt almost any file over a network. A file does not need to be mapped to a particular drive. If the file is present on the same network as an infected end-point, the file is at great risk.
Cerber is to date one of the most successful ransomwares generating over $2 million in revenue. Cerber is still around as a RaaS but is no longer popular due to more robust ransomwares being available on the market. Cerber’s main differentiating feature of being able to attack an entire network has also become more common in other ransomware products.
Cerber spreads through either phishing emails or through infected websites. Cerber only encrypts individual files but we recommend a total OS restore. If you use a service like Zebra Ransomware Stopper, you can grab the latest files Cerber failed to encrypt before engaging a restore.
DoppelPaymer (Grief)
(Image Credit: Bleeping Computer)
The methods that DoppelPaymer uses to request ransom payments from victims are unique, and very aggressive compared to what most gangs will do. DoppelPaymer has been known in the past to actually call and threaten victims with physical harm if they do not pay ransom.
DoppelPaymer is a very smart ransomware that uses a process hacker to terminate much of the defensive capabilities of whichever endpoint it infects. Upon injection DoppelPaymer will terminate a machine’s security, email server, backup, and database processes. The goal is to make it so there is nothing that can disrupt the encryption process for DoppelPaymer.
DoppelPaymer encrypts files, but at times has called victims and threatened harm/extortion. DoppelPaymer maintains a public website where it leaks data for businesses and individuals that fail to pay.
When DoppelPaymer infects a machine, it does not leave a note for a set ransom but rather directs users to a .onion link where they can pay a ransom in cryptocurrency. DoppelPaymer is highly targeted and there is a wide range for historically requested ransoms ranging from thousands to millions. If a user chooses to pay the ransom, this gang expects the user to negotiate the ransom amount and many users find after negotation the requested amount is lowered dramatically.
DoppelPaymer no longer goes by its initial name but has rather re-emerged in 2021 as Grief. You should be on the lookout for untrustworthy emails as that is the primary way DoppelPaymer (Grief) spreads.
Ryuk
(Image Credit: SentinalOne)
What sets Ryuk apart is that it blocks off backups taken on the machine itself. This eliminates the option of restoring from a backup (which may have been taken automatically) stored on the same machine. Organizations should keep offsite backups as a policy. ZebraHost offers fast offsite backups stored in secure data centers.
Ryuk has several dangerous capabilities that have made it renown. Ryuk disables on-machine backups, and several other processes related to security, restoration, and functionality that can bypass encryption. Ryuk can also administer encryption commands remotely.
The worst feature however is that Ryuk can use wake-to-LAN which allows the virus to encrypt machines that are sleeping within a network. This means that Ryuk can, within minutes, encrypt an entire data center, rack, or office.
Ryuk primary spreads through phishing emails.
Lockbit
(Image Credit: The Dfirreport)
Lockbit is a relatively modern ransomware that primarily targets large enterprises. Once Lockbit is manually installed on an endpoint, it can automatically self-propagate. Lockbit runs a PowerShell script which disables security programs and encrypts the host machine. From there, Lockbit seeks other endpoints within the network and can, automatically, without intervention, push the script to other machines and infect them. Lockbit can quickly bring down an entire corporate stack.
Lockbit does not cast a wide net. Lockbit targets are mostly corporate or enterprise-level. Criminals that purchase Lockbit RaaS seek victims that cannot afford to lose data and would find that paying the ransom would cost less than trying to manually recover their data.
Lockbit is an advanced ransomware that culminates many advanced features and practices for ransomware. Lockbit automatically propagates, disables security programs, and spreads via targeted phishing campaigns. This shows that RaaS is improving, and gangs are becoming more methodological.
If you are infected with Lockbit your files will either be .lockbit or .abcd. ABCD is the old name for the ransomware.
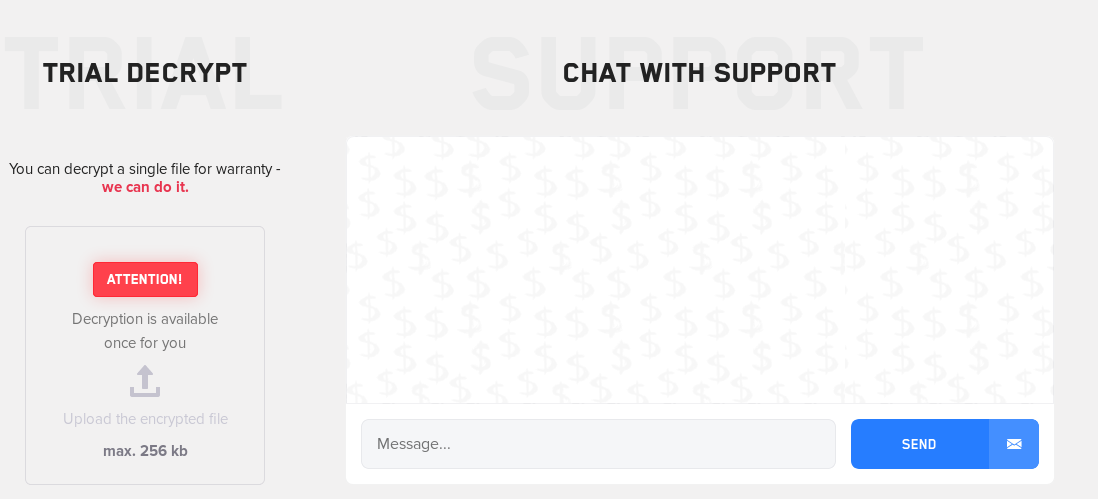
Clop
(Image Credit: Bleeping Computer)
Clop is a ransomware that encrypts files and adds the .clop extension to files.
Clop uses techniques seen in other ransomwares from this list such as disabling security programs and automatically spreading through a LAN network to encrypt all end-points within that network. What makes Clop unique is that rather than focusing on the endpoint, Clop instead focuses on infecting the entire Network by hacking into the Active Directory and determining group policies. From there, Clop can live and issue patches even if end points have already been cleaned. This makes Clop especially dangerous for enterprises.
Clop is known for its extremely aggressive extortion techniques, even using multiple layers of extortion. After infection, Clop steals all the data in an endpoint before encrypting the files. The attackers then threaten to publish the data on their public facing website. If their initial contact does not comply, attackers are known to threaten members of the executive team and even contact clients who they hope will convince their target to pay the ransom.
Clop primary spreads through mass phishing campaigns but can also spread via RDP attack.
Historically Significant Ransomwares
While the previous list of ransomwares are a threat today, there are now countless obsolete ransomwares. Ransomwares do not have a long shelf life and typically die for a variety of reasons. Common reasons include widespread decryption keys available on the open internet, authorities disrupting ransomware gangs’ operations, and gangs shutting their project down because more advanced ransomware is stealing marketshare.
But sometimes uncommon reasons to shutdown exist such as the case of the very successful GandCrab ransomware which netted about $2 million, and the developers felt it was successful enough to shut the ransomware down and publicly released decrypting keys.
Here is a list of some very high profile ransomware attacks that have historically been a major problem and led to the innovations we see in modern ransomwares.
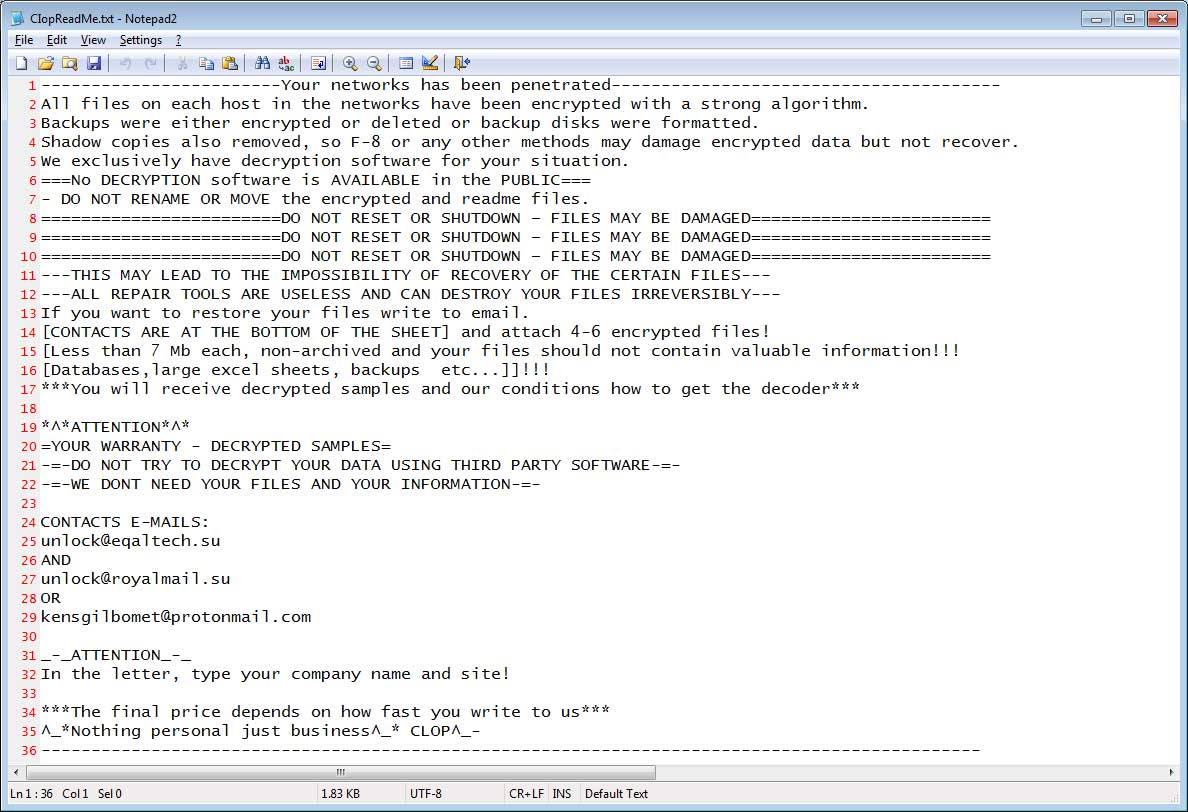
WannaCry
(Image Credit: Wikipedia)
The 2017 WannaCry ransomware is what many think of when they think of ransomware. WannaCry developed into a crisis hitting hundreds of thousands of individuals and organizations and drew major media coverage. The most well known victim was the UK’s National Healthcare Service. WannaCry caused billions of dollars of damages.
Interestingly enough, despite having some of the widest reach of any ransomware attack in history WannaCry was not financially successful. It generated $130,000 which, compared to other succesful ransomwares with less reach, was a low revenue.
WannaCry had a reputation for not providing decrypting keys upon paying ransom, which likely deterred those that would have paid the ransom.
WannaCry was also a very simple ransomware. It only encrypted files and did not use advanced tactics like spreading within a network, extorting victims, or disabling the bootloader.
The result of this was that discovered it was relatively easy to restore data from a backup and avoid paying ransom. Unfortunately, this still means organizations would suffer from outdated data and would need to spend resources restoring data as best they could. Organizations would also still need to cleanse systems in the network meaning that even if ransom wasn’t paid it would still cost victims a lot. Most businesses impacted by WannaCry found that the restoration proces was more expensive than the ransom itself. The NHS for example spent over 6 million pounds restoring their systems.
But the legacy of WannaCry still lives on. It displayed how prolific ransomware can be and has been the driving force behind organizations investing in cyber security and backups. Simple ransomware like WannaCry is easily stopped in milliseconds by Zebra Ransomware Stopper.
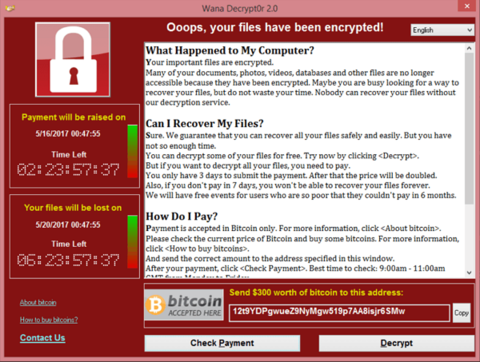
GandCrab
GandCrab was the most prolific ransomware in 2019. Its even said that at GandCrab’s peak, it represented 50% of the ransomware market.
GandCrab was also the most profitable ransomware in history. According to the developers GandCrab netted over $2 billion before the founders decided to close shop. Though this number has been refuted, the amount eclipses what even some of the most succesful ransomware projects would make.
GandCrab was the gold standard for ransomware as a service (RaaS). There were 5 version created and each version enhanced features and made current publicly available decryption keys useless. This constant support made GandCrab extremely successful as a service because forks were not required once decryption keys were available like for most other ransomware projects.
GandCrab would spread via web pop-up ads, phishing emails, and brute force RDP attacks. Once on the computer it would execute a PowerShell script to disable programs on Windows machines and begin encrypting files with the .crab extension. A note was placed on desktop with instructions on how to pay, TOR installed, and the wallpaper changed to let users know their machine was encrypted.
What made GandCrab unique was that it was a fileless ransomware meaning that no additional code had to be installed on the computer. It simply exploited permissions and used tools built into the OS to encrypt files. This made GandCrab very difficult to remove. And because the developer was so active, for the entire existence of the program, security firms failed to put out effective decryption keys. When Bitdefender put out their decryption key, GandCrab was updated to counteract it.
To this day there has never been a ransomware that is as well managed as a service as GandCrab. It served as the gold standard for what RaaS is capable of.
And although GandCrab is no longer around (at least that we know of) after the creators decided they made enough money and closed shop, there’s no guarantee the project cant be copied or forked in the future. Or that GandCrab itself returns.
CryptoLocker
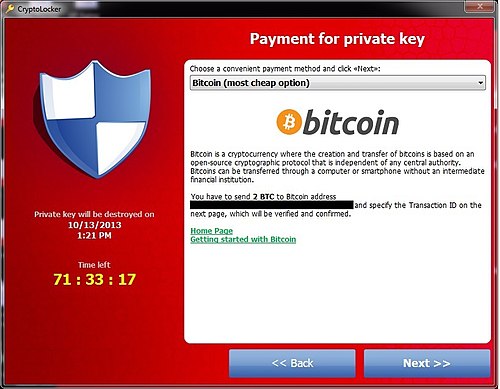
CryptoLocker is the other ransomware people think of when they think of ransomware. CryptoLocker was active 2013-2014.
Crypto Locker would deploy via phishing campaigns. Attackers would infiltrate organizations by sending an email with a .exe attachment disguised as a PDF file. By default, Windows only shows the file name and icon. This means attackers were able to easily fool users simpy by using the PDF file icon for the .exe.Once clicked, CryptoLocker would not only encrypt files on the host machine, but also propagate and infect other machines on the network.
What is interesting about CryptoLocker is that it would not encrypt every file on a machine but rather only encrypt files with extensions that are associated with important data. Files like pictures, Office documents, and AutoCAD files (.DWG).
CryptoLocker was especially dangerous because it was very difficult to crack at first and there was little alternative to paying the ransom. Eventually in 2014 a Dutch firm was able to create a decryption tool that provide users with a private key upon uploading a file sample.
Its believed CryptoLocker made about $3 million before shutting down.
AIDS Ransomware

AIDS was the first recorded successful ransomware attack in history. It would replace the AUTOEXEC.BAT file and then count the number of times a computer has been rebooted. After 90 reboots the ransomware would then encrypt all the files in the cDrive. The only way to receive the proper key to recover the files was to mail the attacker a cash payment.
Due to the limitations of the then fledgling computing space, the AIDS ransomware was highly targeted. A floppy disk was mailed to those subscribed to the WHO’s AIDS conference. When victims inserted the floppy disk and downloaded the software, they had to agree to an agreement that if they do not pay for the software, they are liable for outstanding debts.
The creator of the AIDS ransomware Joseph Popp was easily caught due to his high profile. He was educated at Harvard, work with The African Medical Research Foundation (AMREF), and worked with the WHO regarding the AIDS virus. The fact that the money had to be sent physically also created a convenient trail. Now days, the challenge for cybercriminals regarding anonymity has, for the most part, been solved through innovations like the anonymous relay browser TOR, Cryptocurrency, and criminals working in nations that have poor or non-existing diplomatic ties with nations attackers target.
Summary
Ransomware is a modern invention with a relatively short history. But there have been monumental leaps that have transformed ransomware from lone-wolf projects to an entire industry. Ransomware has become increasingly sophisticated and no longer has the simple goal of encrypting files, but rather now focuses on holding data captive and even acquiring it for leaking or selling. Ransomware has also changed dramatically focusing on sophisticated phishing attacks that target large businesses that cannot afford data loss or downtime.
The different ransomwares on this list provide a look at how quickly ransomware has advanced. While not exhaustive, these ransomwares show the features shared in many ransomware projects today. Ransomware as a service has increased the frequency projects like those on this list are forked and cloned.
To protect yourself you must make sure to keep offsite, and preferably offline, backups that can be restored from outside your network. This will ensure that even if your entire network becomes infected you still have a way to restore your data. If you are in an industry like Healthcare that must keep long-term records, consider immutable backups as well which are backups that cannot be modified. Cold storage backups such as tapes are also a great option.
When it comes to preventative tools, we recommend having a full cybersecurity stack consisting of anti-virus, firewall, tools to manage permissions, password safes, and dedicated ransomware defense. Tools like Zebra Ransomware Stopper can stop ransomware in milliseconds, preventing it form taking over your computer or spreading within your network. It functions like deploying decoy files that act as atrip wire so when a ransomware begins an encryption file, the files detect and halt the encryption process. Click here to learn more about how ZRS can benefit your security stack.